srcScan,subfinder域名爆破,ksubdomain验证,httpx资产存活验证:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 function show_help { echo "Usage: $0 [-d DOMAIN] [-f FILE]" echo " -d DOMAIN The domain name to search for." echo " -f FILE A file containing a list of domains to search for, one per line." echo " -h, --help Show this help message and exit." } while getopts ":d:f:h" opt; do case $opt in d) domain=$OPTARG ;; f) file=$OPTARG ;; h | *) show_help exit 0 ;; esac done if [ -z "$domain " ] && [ -z "$file " ]; then echo "No domain or file specified. Usage: $0 -d example.com OR $0 -f domains.txt" >&2 exit 1 fi if [ ! -z "$domain " ]; then ./subfinder -dL $domain -silent | ./ksubdomain -verify -silent | ./httpx -mc 200,302 -t 200 --random-agent fi if [ ! -z "$file " ]; then ./subfinder -dL $file -silent | ./ksubdomain -verify -silent | ./httpx -mc 200,302 -t 200 -random-agent fi
域名收集加网址提取:
1 2 3 ./subfinder -dL domain.txt -silent | ./ksubdomain -verify -silent | ./naabu -top-ports 100 -silent | ./httpx -t 300 -mc 200,302 --random-agent -o url.txt //省略-o参数-silent后面还可以继续拼接工具,例如nuclei xpoc等
XSS Scan:
1 2 3 4 5 ./xray ws --listen 127.0.0.1:7777 -plugins xss --ho scan.html ./subfinder -dL domain.txt -silent | ./ksubdomain -verify -silent | ./httpx -t 300 -mc 200,302 --random-agent -p 80,8080,443,8090,9090 -silent | ./hakrawler -d 5 -dr -t 50 -u -proxy <http://127.0.0.1:7777> //xray监听本地端口扫描XSS漏洞,hakrawler对资产自动爬取通过代理推送给xray端口
参数爬取:
1 2 3 4 5 6 7 cat url.txt | ./hakrawler -d 5 -dr -t 50 -u//hakrawler通过网站sitemap.xml文件扫描参数,可配合xray代理推送 python3 paramspider.py -d domain //paramspider通过国外在线网站进行FUZZ参数
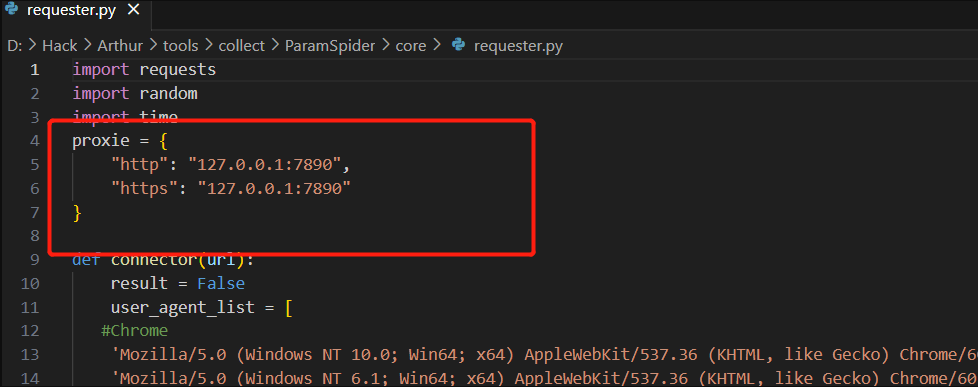
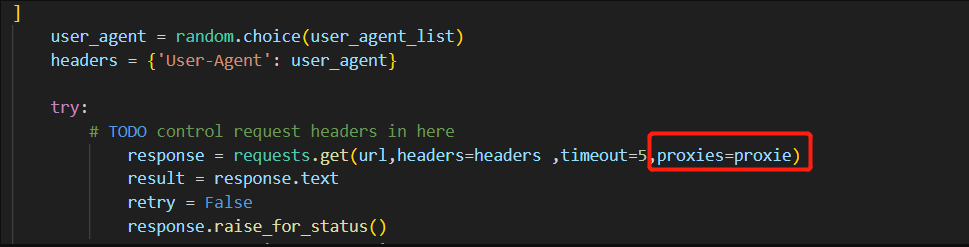
paramspider.py使用过程需要增加一个代理,core/requester.py中
1 2 3 4 5 6 7 8 proxie = { "http" : "127.0.0.1:7890" , "https" : "127.0.0.1:7890" } · · · response = requests.get(url,headers=headers ,timeout =5,proxies=proxie)
域名爆破+端口扫描+网址验证+poc扫描:
1 2 3 ./subfinder -dL domain.txt -silent | ./ksubdomain -verify -silent | ./naabu -top-ports 100 -silent | ./httpx -t 300 -mc 200,302 --random-agent -silent | ./nuclei -s medium,high,critical -rate-limit 100 -bulk-size 25 -concurrency 25 -stats -si 300 -retries 3 ./subfinder -dL domain.txt -silent | ./ksubdomain -verify -silent | ./naabu -top-ports 100 -silent | ./httpx -t 300 -mc 200,302 --random-agent -silent | ./xpoc -o scan.html
FUZZ扫描,适合单个资产,yawf扫描速度慢:
1 2 3 rad --uf url.txt --json scan.json python3 yawf_bulk.py -f scan.json
通过ParamSpider爬取参数,推送给yawf让其对参数批量FUZZ扫描,yawf_file.py:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from os import system import argparse def scan_file(file): with open(file, encoding='utf-8' ) as f: lines = f.readlines() total_uris = len(lines) for index, uri in enumerate(lines, 1): print (f'[*] Processing ({index}/{total_uris}) {uri.strip()}' ) system(f'python yawf.py -u {uri.strip()}' ) def main(): parser = argparse.ArgumentParser(description='yawf File Mode Help' ) parser.add_argument('-f' , '--file' , help ='Yawf 批量扫描' , default='' ) args = parser.parse_args() if args.file: file = args.file scan_file(file) if __name__ == '__main__' : main()
FoFaX资产测绘推送给poc扫描工具:
1 2 3 4 5 6 7 8 ./fofax -q domain="baidu.com" -silent | ./xpoc -o scan.html ./fofax -qf search.txt -silent | ./xpoc -o scan.html search.txt: domain="baidu.com" ip="1.1.1.1" title="系统"
更进一步,域名爆破验证,shell命令自动将域名结果加入domain=””格式,再利用FoFaX批量扫描资产,推送给漏扫工具,下面是批量给域名加入domain=””格式,方便推送FoFaX批量查找:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 # !/bin/bash # 读取domain.txt文件内容 while IFS= read -r line; do # 将域名结果加入domain="" 格式 result="domain=\"$line\"" # 将结果写入临时文件 echo "$result" >> temp.txt done < domain.txt # 将临时文件覆盖原有文件 mv temp.txt domain.txt //简便命令: sed -i 's/^/domain="/;s/$/"/' domain.txt