首先,未配置脚本时,打开APP开启BP抓包,此时无法抓取到数据包,提示certificate_unknown,即证书错误,那么大概率是使用了SSL Pinning方法。
使用adb connect连接到模拟器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 adb connect 127.0 .0 .1 :62001 adb server is out of date. killing... * daemon started successfully * connected to 127.0 .0 .1 :62001 C :\\Users >adb devicesList of devices attached127.0 .0 .1 :62001 deviceC :\\Users >adb shell8beyond1q :/ # su beyond1q :/ # cd / data/local/tmpcd /data/local/tmp beyond1q :/data/ local/tmp # lsfrida-server-14.2 .18 -android-x86 hluda-server-14.2 .18 -android-x86 beyond1q :/data/ local/tmp # ./hluda-server-14.2 .18 -android-x86
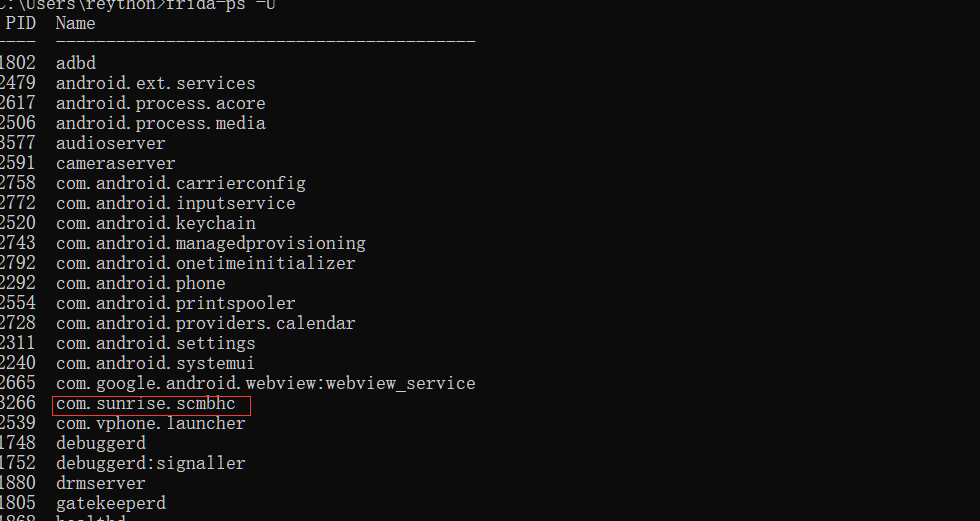
运行hluda-server之后,新开一个窗口,使用frida-ps -U命令获取目标包名(此时目标应处于打开状态)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 frida-ps -U PID Name ---- ------------------------------------------ 1802 adbd2479 android.ext .services 2617 android.process .acore 2506 android.process .media 3577 audioserver2591 cameraserver2758 com.android .carrierconfig 2772 com.android .inputservice 2520 com.android .keychain 2743 com.android .managedprovisioning 2792 com.android .onetimeinitializer 2292 com.android .phone 2554 com.android .printspooler 2728 com.android .providers .calendar 2311 com.android .settings 2240 com.android .systemui 2665 com.google .android .webview :webview_service3266 com.sunrise .scmbhc 2539 com.vphone .launcher 1748 debuggerd
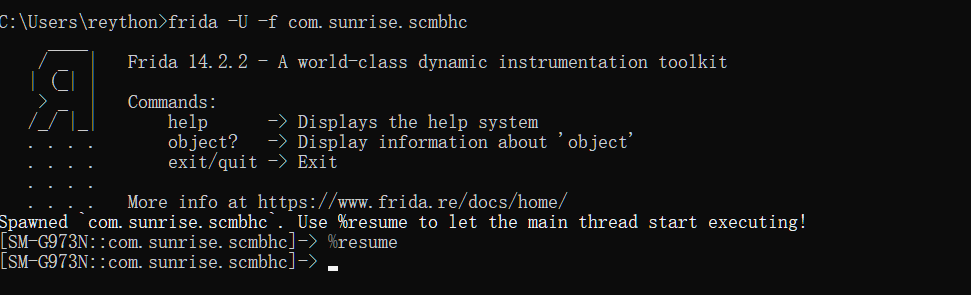
获取到目标之后,使用frida -f -U com.xxx.xxx命令注入目标进程
1 2 3 4 5 6 7 8 9 10 11 12 13 frida -U -f com.sunrise .scmbhc ____ / _ | Frida 14.2 .2 - A world-class dynamic instrumentation toolkit | (_| | > _ | Commands : /_/ |_| help -> Displays the help system . . . . object? -> Display information about 'object' . . . . exit/quit -> Exit . . . . . . . . More info at <https : Spawned `com.sunrise.scmbhc` . Use %resume to let the main thread start executing![SM -G973N ::com.sunrise .scmbhc ]-> %resume [SM -G973N ::com.sunrise .scmbhc ]->
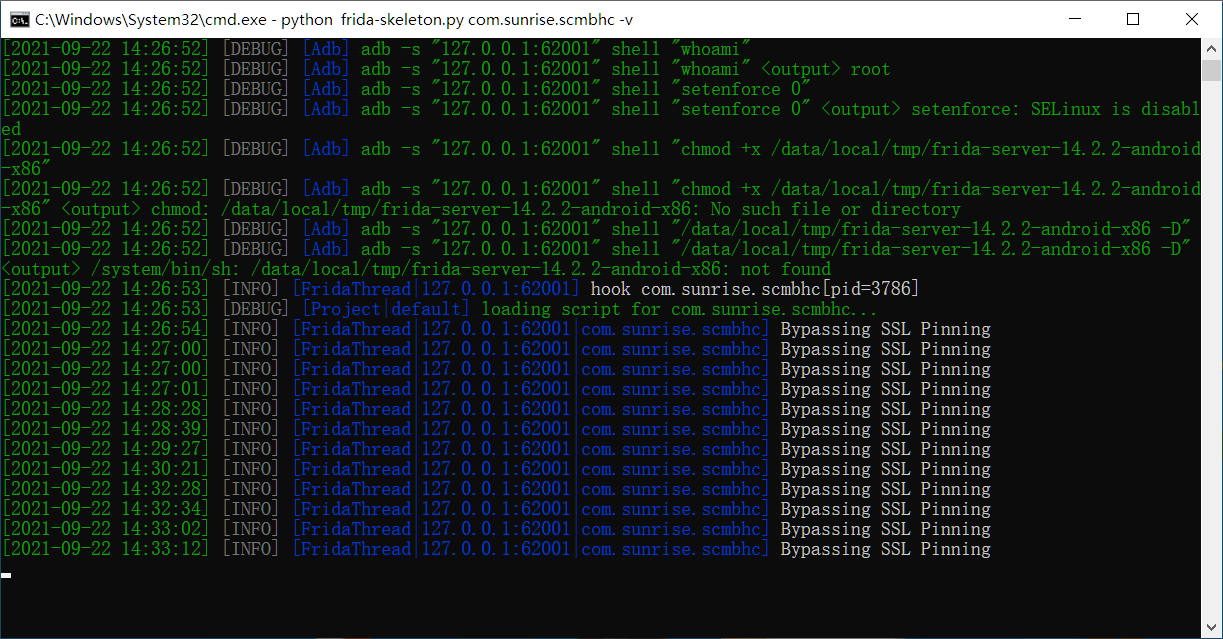
之后再次新开窗口,进入feida-skeleton脚本目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 python frida-skeleton.py -h usage : frida-skeleton.py [-h] [-l] [-d DEVICES ] [-i] [-p PORT ] [-s] [-v] [regexps [regexps ...]]基于frida的安卓hook框架,提供了很多frida自身不支持的功能,将hook安卓变成简单便捷,人人都会的事情,项目地址:<https : positional arguments : regexps 根据你指定的正则表达式去匹配包名hook对应的程序,支持多个正则表达式 optional arguments : -h, --help show this help message and exit -l, --list 显示设备列表 -d DEVICES , --devices DEVICES 指定hook的设备,多个设备逗号隔开 -i, --install 自动从github安装对应版本和架构的frida-server到assets目录下,支持断点续传,下载完后自动运行 -p PORT , --port PORT 自动利用iptables和adb将所有的TCP 流量重定向到PC 的指定端口,这样就可以在本机监听该端口来抓包了 -s, --spawn 开启frida的spawn模式并忽略项目配置文件中的spawn选项,开启此选项会导致被hook的进程自动重启 -v, --verbose 输出调试信息 python frida-skeleton.py com.sunrise .scmbhc -v [2021 -09 -22 14 :26 :51 ] [DEBUG ] [Shell ] adb start-server [2021 -09 -22 14 :26 :51 ] [DEBUG ] [Shell ] adb start-server <output> Nothing [2021 -09 -22 14 :26 :51 ] [DEBUG ] [WatchThread ] WatchThread start [2021 -09 -22 14 :26 :52 ] [DEBUG ] [FridaThread |127.0 .0 .1 :62001 ] device 127.0 .0 .1 :62001 does not support get_usb_device, changing to get_remote_device method [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "whoami" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "whoami" <output> root [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" forward tcp :61280 tcp :27042 [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" forward tcp :61280 tcp :27042 <output> Nothing [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "getprop ro.product.cpu.abi" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "getprop ro.product.cpu.abi" <output> x86 [2021 -09 -22 14 :26 :52 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 ] FridaThread start with hook device : id=127.0 .0 .1 :62001 , name=127.0 .0 .1 :61280 , type=remote [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" root [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" root <output> adbd is already running as root [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "whoami" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "whoami" <output> root [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "setenforce 0" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "setenforce 0" <output> setenforce : SELinux is disabled [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "chmod +x /data/local/tmp/frida-server-14.2.2-android-x86" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "chmod +x /data/local/tmp/frida-server-14.2.2-android-x86" <output> chmod : /data/ local/tmp/frida-server-14.2 .2 -android-x86 : No such file or directory [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "/data/local/tmp/frida-server-14.2.2-android-x86 -D" [2021 -09 -22 14 :26 :52 ] [DEBUG ] [Adb ] adb -s "127.0.0.1:62001" shell "/data/local/tmp/frida-server-14.2.2-android-x86 -D" <output> /system/ bin/sh : /data/ local/tmp/frida-server-14.2 .2 -android-x86 : not found [2021 -09 -22 14 :26 :53 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 ] hook com.sunrise .scmbhc [pid=3786 ] [2021 -09 -22 14 :26 :53 ] [DEBUG ] [Project |default ] loading script for com.sunrise .scmbhc ... [2021 -09 -22 14 :26 :54 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :27 :00 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :27 :00 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :27 :01 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :28 :28 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :28 :39 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :29 :27 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :30 :21 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :32 :28 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :32 :34 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :33 :02 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning [2021 -09 -22 14 :33 :12 ] [INFO ] [FridaThread |127.0 .0 .1 :62001 |com.sunrise .scmbhc ] Bypassing SSL Pinning
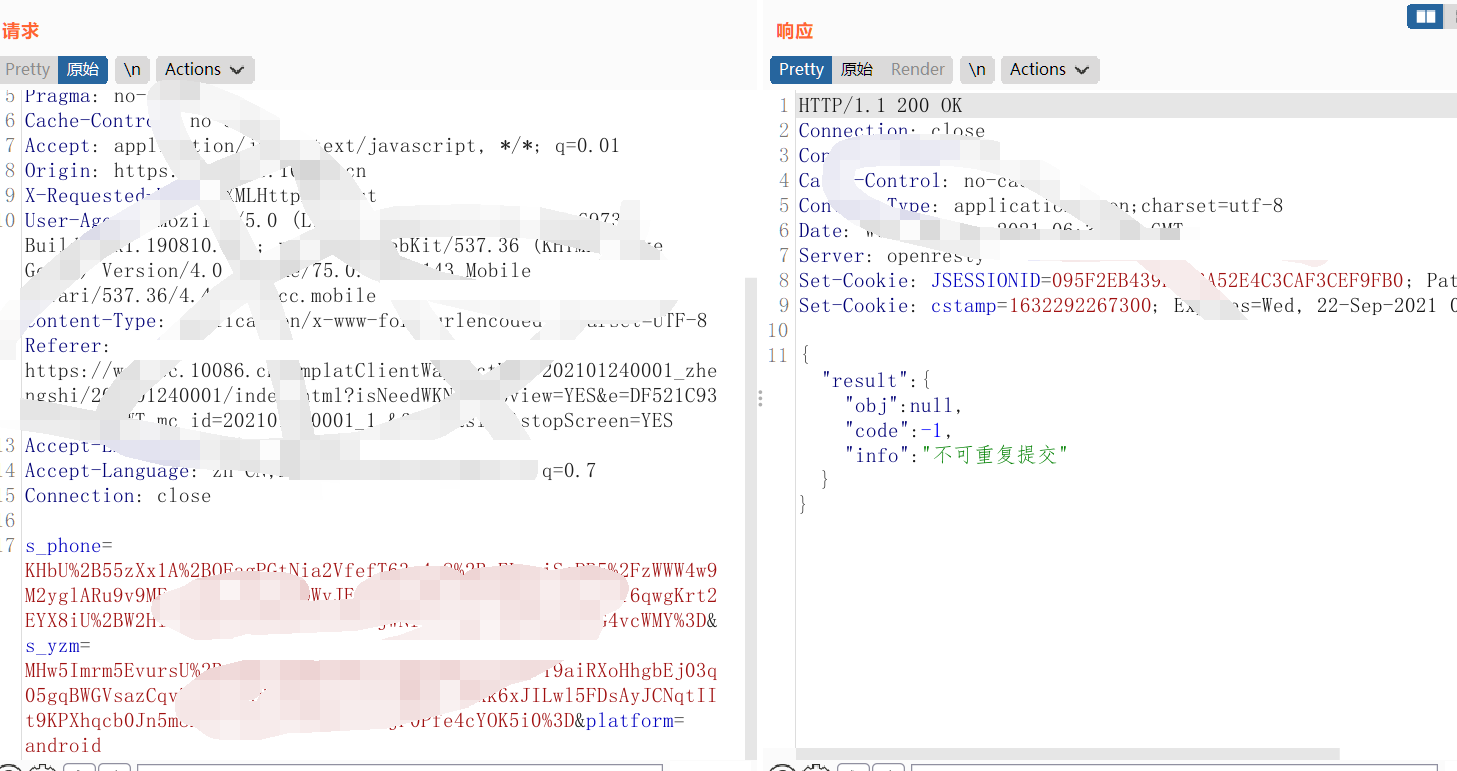
此时再次尝试抓取数据包: